ISA 2000 - Policy Elements

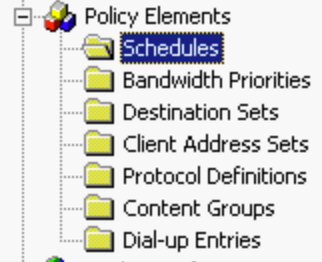
- Schedules - hours for which the policy is active/inactive
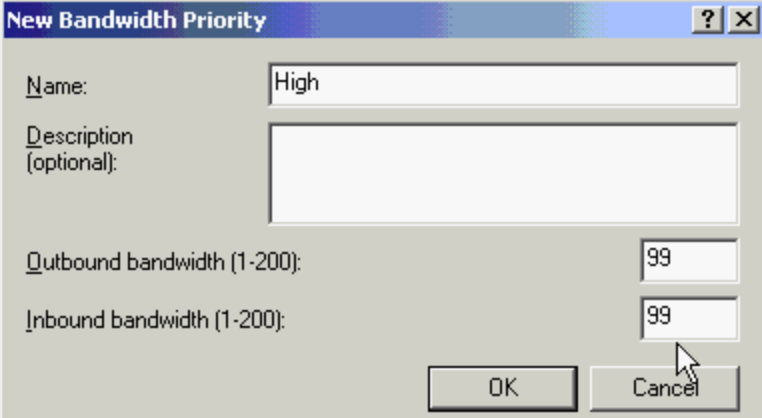
- Bandwidth Priorities - prioritise traffic types - range 1 -200 compared as a ratio to other priorities

- Destination Sets
- Client Address sets
- Protocol definitions (most common are defined by default)
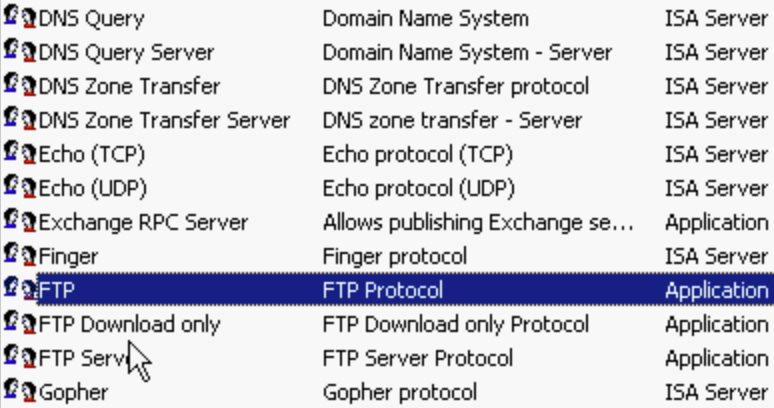
- Content Groups - MIME Types
- Dial-up Entries - backup connection using modem
Rules
Order of processing:
- Does a protocol rule deny the request
- Does a protocol rule allow the request
- Does a site & content rule deny the request
- Does a site & content rule allow the request
- Does a packet filter block the request
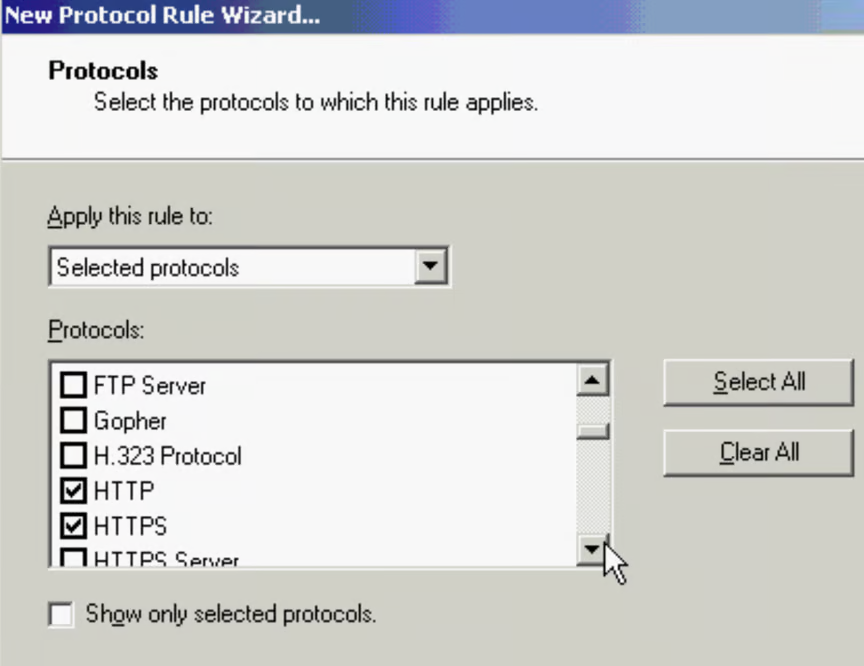
Protocol Rule
No protocol rule is created by default; all traffic will be denied.
Site and Content Rules
Allow any rule is created by default.
Can redirect denied HTTP requests
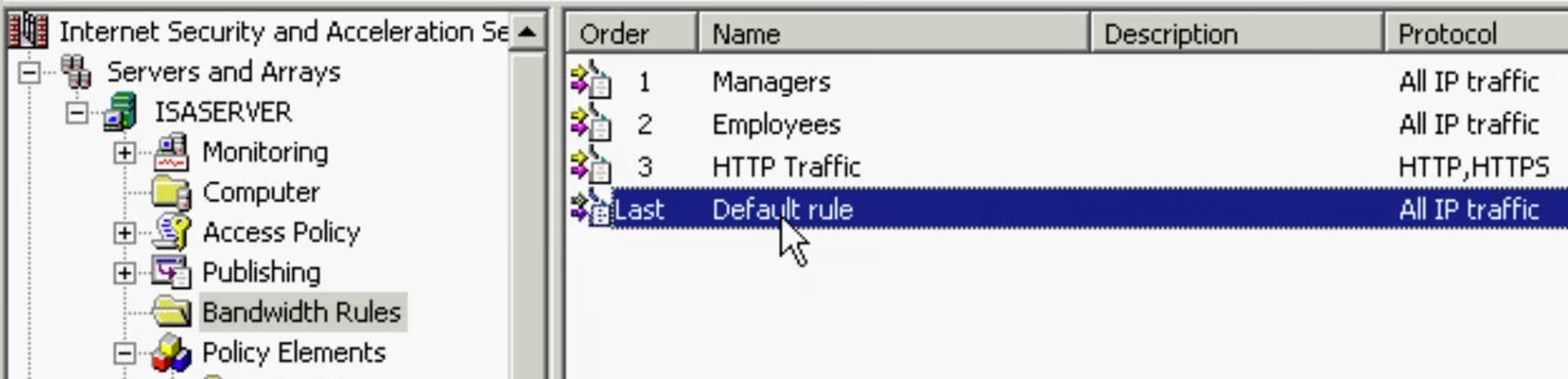
Bandwidth Rules
Bandwidth by ratio
- Network Allocation - traffic types
- User Allocation - groups
- Unused priorities - if reserved used, can be used by others
- rule order - first rule that matches
- default rule - if not matching other rules
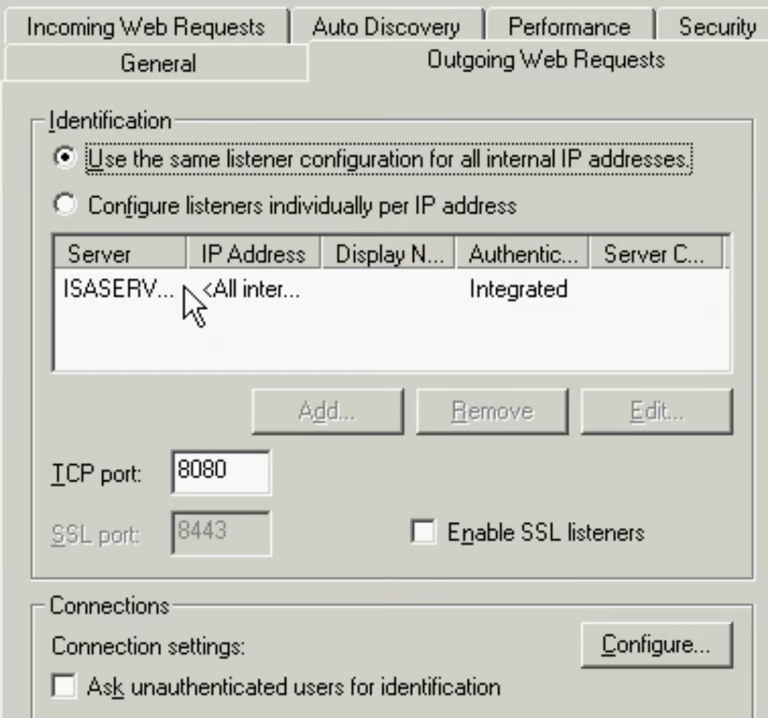
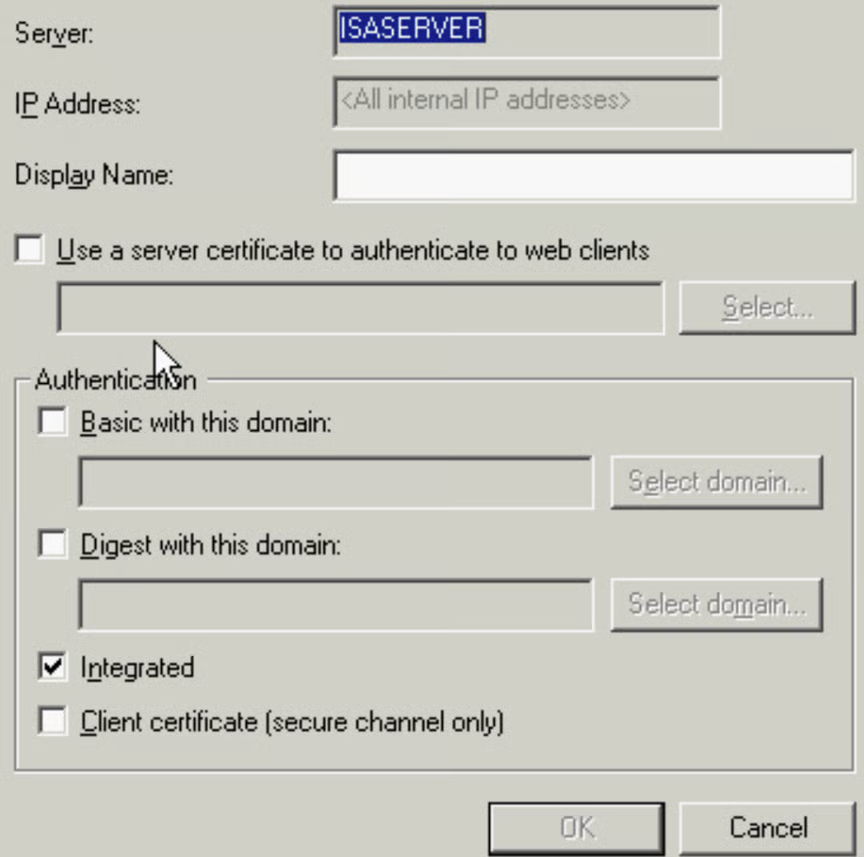
Authentication
SecureNAT client - no auth - no user or group restrictionsFirewall Client - requires install, only Windows devicesWeb Proxy Clients - can use auth
- Basic Authentication - any device can support, details sent in clear text
- Digest Authentication - Requires IE 5.0+
- Integrated Windows Authentication - Kerberos , IE 2.0+
- Client Certificate Authentication - every client needs a certificate
Enabled per-server, needs to restart services. Default is integrated