DAI - Dynamic ARP Inspection

Prevents ARP poisoning/spoofing attacks.
- Uses the DHCP Snooping database
- Can use static ARP ACL to map
- Header to Payload validation
- Ports can be trusted to disable inspection, typically trust trunk ports.
- Violation of rate limiting puts port in error disabled state.
Configuration
ip arp inspection vlan 123
int gi1/0/1
ip arp inspection trustRate limiting on client access ports.
int range gi1/0/3-24
ip arp inspection limit rate 10Access list for devices with static (non-DHCP) IP addresses.
arp access-list ARP-ACL
permit ip host 10.123.0.1 mac host 0000.0000.0000
ip arp inspection filter ARP-ACL vlan 123Enable payload validation
ip arp inspection validate src-mac dst-mac ipEnable auto recovery of disabled ports
errdisable recovery cause arp-inspection
errdisable recovery interval 30Verification commands
show ip arp inspection vlan 123
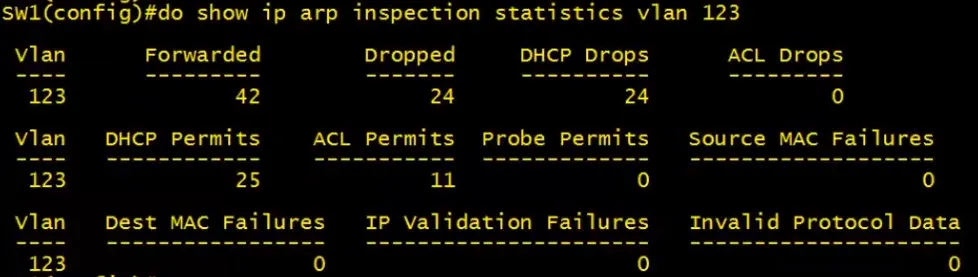
show ip arp inspection statistics vlan 123
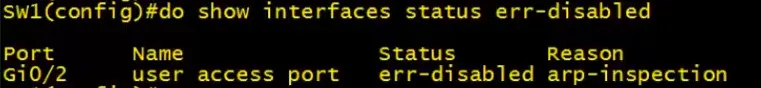
show interfaces status err-disabled